
64
Chapter 3. Installing Red Hat Linux
Tip
To change your user account configuration after you have completed the installation, use the User
Manager.
Type the redhat config users command in a shell prompt to launch the User Manager. If you are
not root, it will prompt you for the root password to continue.
3.26. Authentication Configuration
If you are performing a personal desktop, workstation or server installation, please skip ahead to
Section 3.27.
You may skip this section if you will not be setting up network passwords. If you do not know whether
you should do this, please ask your system administrator for assistance.
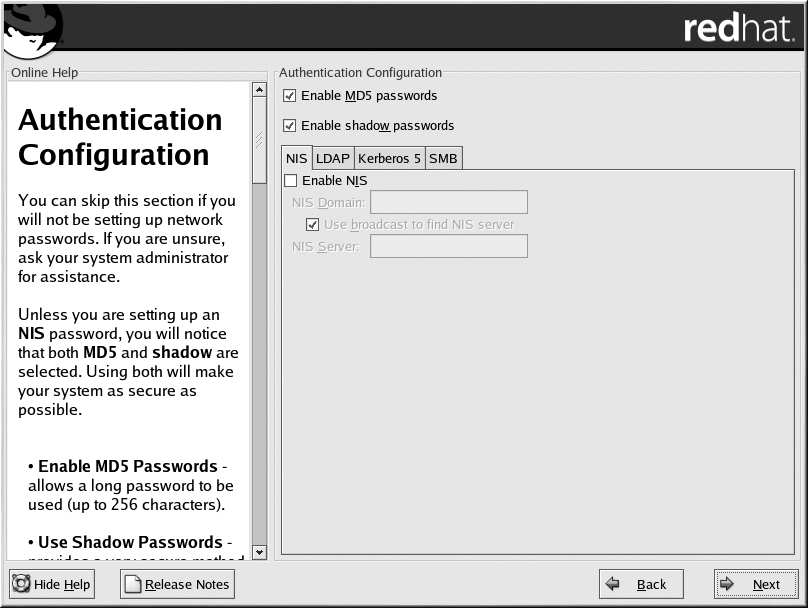
Unless you are setting up NIS authentication, you will notice that only MD5 and shadow passwords
are selected (see Figure 3 24). We recommend you use both to make your machine as secure as
possible.
To configure the NIS option, you must be connected to an NIS network. If you are not sure whether
you are connected to an NIS network, please ask your system administrator.
Figure 3 24. Authentication Configuration
Enable MD5 passwords allows a long password to be used (up to 256 characters), instead of
the standard eight characters or less.
Enable shadow passwords provides a secure method for retaining passwords. The passwords
are stored in
/etc/shadow
, which can only be read by root.
Enable NIS allows you to run a group of computers in the same Network Information Service
domain with a common password and group file. You can choose from the following options:
footer
Our partners:
PHP: Hypertext Preprocessor Best Web Hosting
Java Web Hosting
Inexpensive Web Hosting
Jsp Web Hosting
Cheapest Web Hosting
Jsp Hosting
Cheap Hosting
Visionwebhosting.net Business web hosting division of Web
Design Plus. All rights reserved
