
Chapter 3. Installing Red Hat Linux
57
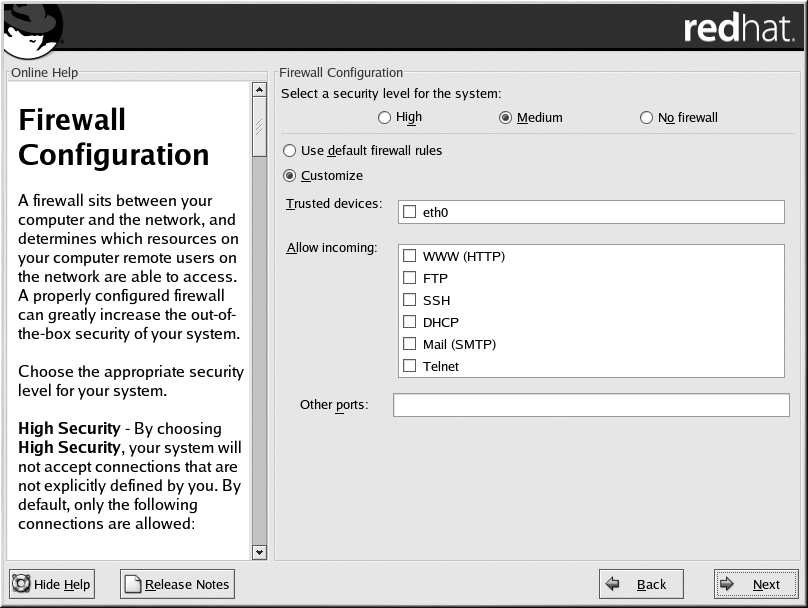
3.22. Firewall Configuration
Red Hat Linux offers firewall protection for enhanced system security. A firewall exists between your
computer and the network, and determines which resources on your computer remote users on the
network can access. A properly configured firewall can greatly increase the security of your system.
Figure 3 19. Firewall Configuration
Choose the appropriate security level for your system.
High
If you choose High, your system will not accept connections (other than the default settings) that
are not explicitly defined by you. By default, only the following connections are allowed:
DNS replies
DHCP so any network interfaces that use DHCP can be properly configured
If you choose High, your firewall will not allow the following:
Active mode FTP (passive mode FTP, used by default in most clients, should still work)
IRC DCC file transfers
RealAudio
Remote X Window System clients
If you are connecting your system to the Internet, but do not plan to run a server, this is the safest
choice. If additional services are needed, you can choose Customize to allow specific services
through the firewall.
Note
If you select a medium or high firewall to be setup during this installation, network authentication
methods (NIS and LDAP) will not work.
footer
Our partners:
PHP: Hypertext Preprocessor Best Web Hosting
Java Web Hosting
Inexpensive Web Hosting
Jsp Web Hosting
Cheapest Web Hosting
Jsp Hosting
Cheap Hosting
Visionwebhosting.net Business web hosting division of Web
Design Plus. All rights reserved

