
18
Chapter 1 Introduction to Intrusion Detection and Snort
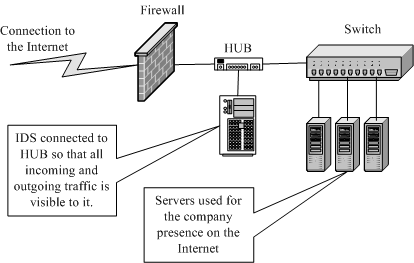
Figure 1 8 Connecting an IDS in a switched environment.
Note that when the IDS is connected as shown in Figure 1 8, data flowing among
the company servers is not visible to the IDS. The IDS can see only that data which is
coming from or going to the Internet. This is useful if you expect attacks from outside
and the internal network is a trusted one.
1.5 TCP Stream Follow Up
A new preprocessor named Stream4 has been added to Snort. This preprocessor is capa
ble of dealing with thousands of simultaneous streams and its configuration will be dis
cussed in Chapter 4. It allows TCP stream reassembly and stateful inspection of TCP
packets. This means that you can assemble packets in a particular TCP session to find
anomalies and attacks that use multiple TCP packets. You can also look for packets
coming to and/or originating from a particular server port.
1.6 Supported Platforms
Snort is supported on a number of hardware platforms and operating systems. Currently
Snort is available for the following operating systems:
Linux
OpenBSD
footer
Our partners:
PHP: Hypertext Preprocessor Cheap Web Hosting
JSP Web Hosting
Ontario Web Hosting
Jsp Web Hosting
Cheapest Web Hosting
Java Hosting
Cheapest Hosting
Visionwebhosting.net Business web hosting division of Vision Web Hosting Inc.. All rights reserved


