
What is Intrusion Detection?
5
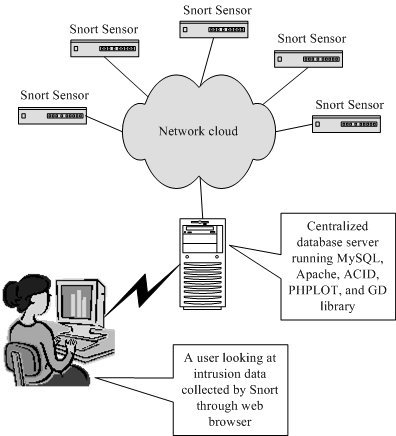
Figure 1 3 Multiple Snort sensors in the enterprise logging to a centralized database server.
1.1 What is Intrusion Detection?
Intrusion detection is a set of techniques and methods that are used to detect suspi
cious activity both at the network and host level. Intrusion detection systems fall into
two basic categories: signature based intrusion detection systems and anomaly detec
tion systems. Intruders have signatures, like computer viruses, that can be detected
using software. You try to find data packets that contain any known intrusion related
signatures or anomalies related to Internet protocols. Based upon a set of signatures
and rules, the detection system is able to find and log suspicious activity and generate
alerts. Anomaly based intrusion detection usually depends on packet anomalies
present in protocol header parts. In some cases these methods produce better results
compared to signature based IDS. Usually an intrusion detection system captures
data from the network and applies its rules to that data or detects anomalies in it.
Snort is primarily a rule based IDS, however input plug ins are present to detect
anomalies in protocol headers.
footer
Our partners:
PHP: Hypertext Preprocessor Cheap Web Hosting
JSP Web Hosting
Ontario Web Hosting
Jsp Web Hosting
Cheapest Web Hosting
Java Hosting
Cheapest Hosting
Visionwebhosting.net Business web hosting division of Vision Web Hosting Inc.. All rights reserved


