84
Chapter 9. Vulnerability Assessment
The results of the scan (which could take up to a few minutes, depending on where the host is located)
should look similar to the following:
nmap 127.0.0.1
Starting nmap V. 3.00 ( www.insecure.org/nmap/ )
Interesting ports on localhost.localdomain (127.0.0.1):
(The 1591 ports scanned but not shown below are in state: closed)
Port
State
Service
22/tcp
open
ssh
25/tcp
open
smtp
111/tcp
open
sunrpc
515/tcp
open
printer
950/tcp
open
oftep rpc
6000/tcp
open
X11
Nmap run completed 1 IP address (1 host up) scanned in 0 seconds
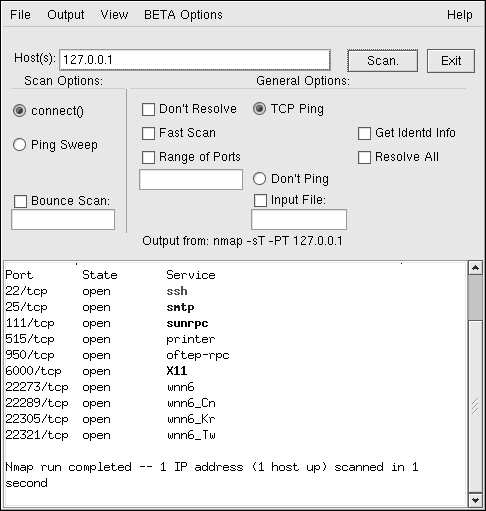
If you were to use the graphical version (which can be run by typing
/usr/bin/nmapfe
at a shell
prompt), the results will look similar to the following:
Figure 9 1. Scanning with Nmap
Nmap tests the most common network communication ports for listening or waiting services. This
knowledge can be helpful to an administrator who wants to, for example, close down unnecessary
services.
For more information about using Nmap, refer to the official homepage at http://www.insecure.org.
footer
Our partners:
PHP: Hypertext Preprocessor Best Web Hosting
Java Web Hosting
Inexpensive Web Hosting
Jsp Web Hosting
Cheapest Web Hosting
Jsp Hosting
Cheap Hosting
Visionwebhosting.net Business web hosting division of Web
Design Plus. All rights reserved

