Chapter 4. Workstation Security
41
When determining whether or not to leave these services running, it is best to use common sense and
err on the side of caution. For instance, if you do not own a printer, do not leave
lpd
running with the
assumption that one day you might buy one. The same is true for
portmap
. If you do not mount NFS
volumes or use NIS (the
ypbind
service), then turn portmap should be disabled.
Red Hat Linux ships with three programs designed to switch services on or off. They are Services
Configuration Tool, ntsysv, and
chkconfig
. For information on using these tools, see the chapter
titled Controlling Access to Services in the Official Red Hat Linux Customization Guide.
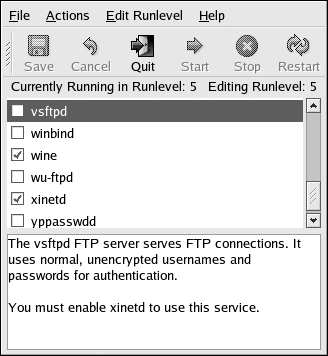
If you are not sure what purpose a service has, the Services Configuration Tool has a description
field, illustrated in Figure 4 3, that may be of some use.
Figure 4 3. User Groups Pane
But checking to see which network services are configured to start at boot time is not enough. Good
system administrators should also check which ports are open and listening. See Section 5.8 for more
on this subject.
4.5.3. Insecure Services
Potentially any network service is insecure. This is why turning unused services off is so important.
Exploits for services are revealed and patched routinely. But you must remember the importance of
keeping the packages associated with any given service updated. See for more on this issue.
Some network protocols are inherently more insecure than others. These include any services which
do the following:
footer
Our partners:
PHP: Hypertext Preprocessor Best Web Hosting
Java Web Hosting
Inexpensive Web Hosting
Jsp Web Hosting
Cheapest Web Hosting
Jsp Hosting
Cheap Hosting
Visionwebhosting.net Business web hosting division of Web
Design Plus. All rights reserved

