
20
Chapter 1 Introduction to Intrusion Detection and Snort
1.7.1
Snort on Stealth Interface
You can run Snort on a stealth interface which only listens to the incoming traffic
but does not send any data packets out. A special cable is used on the stealth interface.
On the host where Snort is running, you have to short pins 1 and 2. Pins 3 and 6 are con
nected to same pins on the other side. Please see Snort FAQ at http://www.snort.org/
docs/faq.html for more information on this arrangement.
1.7.2
Snort with no IP Address Interface
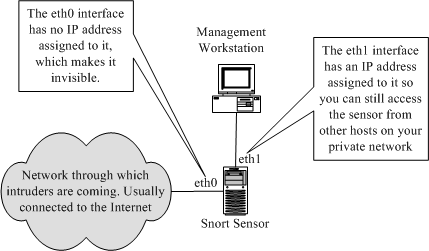
You can also use Snort on an interface where no IP address is assigned. For exam
ple, on a Linux machine, you can bring up interface
eth0
using command
ifconfig
eth0 up
without assigning an actual IP address. The advantage is that when the Snort
host doesn't have an IP address itself, nobody can access it. You can configure an IP
address on eth1 that can be used to access the sensor itself. This is shown in Figure 1 9.
On Microsoft Windows systems, you can use an interface without binding TCP/IP
to the interface, in which case no IP address will be assigned to the interface. Don't for
get to disable other protocols and services on the interface as well. In some cases it has
been noted that winpcap (library used on Microsoft Windows machines to capture
packets) does not work well when no IP address is assigned on the interface. In such a
case, you can use the following method.
Figure 1 9 Snort sensor with two interfaces. One of these has no IP address assigned.
footer
Our partners:
PHP: Hypertext Preprocessor Cheap Web Hosting
JSP Web Hosting
Ontario Web Hosting
Jsp Web Hosting
Cheapest Web Hosting
Java Hosting
Cheapest Hosting
Visionwebhosting.net Business web hosting division of Vision Web Hosting Inc.. All rights reserved


