
8
Chapter 1 Introduction to Intrusion Detection and Snort
and tune different default rules. In some cases you may need to disable some of the
rules to avoid false alarms.
1.1.1.8
Sensor
The machine on which an intrusion detection system is running is also called the
sensor in the literature because it is used to sense the network. Later in this book if the
word sensor is used, it refers to a computer or other device where Snort is running.
1.1.2
Where IDS Should be Placed in Network Topology
Depending upon your network topology, you may want to position intrusion
detection systems at one or more places. It also depends upon what type of intrusion
activities you want to detect: internal, external or both. For example, if you want to
detect only external intrusion activities, and you have only one router connecting to the
Internet, the best place for an intrusion detection system may be just inside the router or
a firewall. If you have multiple paths to the Internet, you may want to place one IDS
box at every entry point. However if you want to detect internal threats as well, you may
want to place a box in every network segment.
In many cases you don't need to have intrusion detection activity in all network
segments and you may want to limit it only to sensitive network areas. Note that more
intrusion detection systems mean more work and more maintenance costs. Your deci
sion really depends upon your security policy, which defines what you really want to
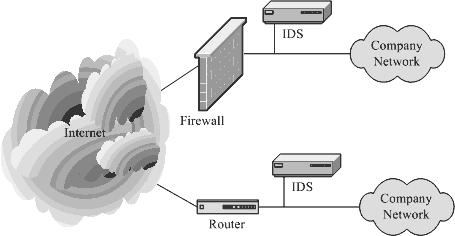
protect from hackers. Figure 1 4 shows typical locations where you can place an intru
sion detection system.
Figure 1 4 Typical locations for an intrusion detection system.
footer
Our partners:
PHP: Hypertext Preprocessor Cheap Web Hosting
JSP Web Hosting
Ontario Web Hosting
Jsp Web Hosting
Cheapest Web Hosting
Java Hosting
Cheapest Hosting
Visionwebhosting.net Business web hosting division of Vision Web Hosting Inc.. All rights reserved


